A few hours ago, the website of popular WordPress plugin WPML (WordPress Multilingual Plugin) got hacked by an ex-employee who had left a backdoor in the site. After hacking, the attacker sent out a mass-mail to every user, stating that the plugin contains several vulnerabilities and warned them to not store any sensitive information on database.
WPML plugin is used to write content in multiple languages and translate content without any need of technical or programming skills. English, Spanish, French, German, Italian and Dutch are the most popular languages on WPML. As per their site, the plugin is currently used by more than 600K WordPress websites.
After hacking the WPML website, the attacker sent the following email to every user:
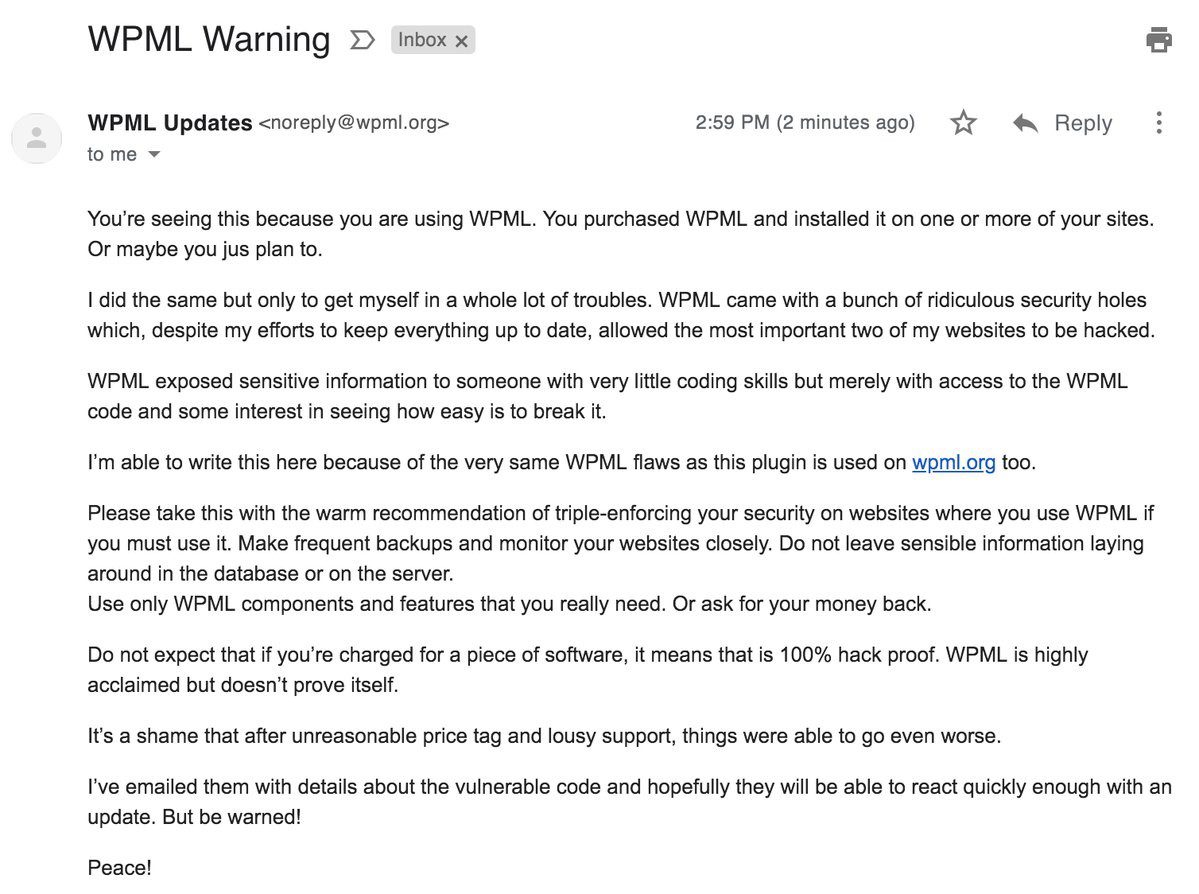
The attacker mentioned in the email that he is a frustrated user of the same plugin who got two of his websites hacked because of security holes in the plugin. Since the same plugin is used by WPML as well, he hacked their website to warn other users.
The attacker also published a blog post on WPML site with the same message that he had sent to users.
However, WPML wrote in a tweet that “Looks like an ex-employee backdoor”. The plugin creator also clarified that they double-checked the plugin, and assured users that there is no exploit. Since the plugin doesn’t store any payment information, there’re no chances of compromising it.
Also read: Plenty of plugins and PHP libraries disabling TLS validation, leaving sensitive data at risk
As of now, WPML has rebuilt its website and suggested the users to update their WPML account password and use a secure one.
We finished rebuilding our https://t.co/PNgrXNs87B site after it was hacked this weekend. Please, be sure to update your WPML account password and use a secure one. Again, the plugin was not compromised. Thanks for all the support messages and apologies for the whole situation.
— WPML (@wpml) January 21, 2019
Update: The title of this news has been updated with feedback from the WPML team. The readers are hereby informed that the plugin was not compromised or hacked and was/is safe to use. The attack was aimed specifically at WPML website.








