YellowPencil, a popular WordPress plugin for visual style editing, has got hacked. Last week, the attackers infected the plugin with a couple of software vulnerabilities that could allow them to update arbitrary options on vulnerable websites.
If any website with active YellowPencil installation is hacked, the attackers gain the ability to make changes to the URLs of the website and the homepage. They could do it using unauthenticated SQL injection.
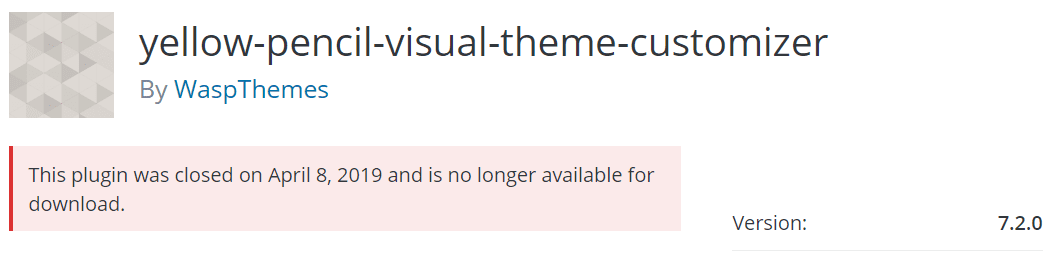
The plugin has more 36,000 downloads, which means that the number of vulnerable websites was high. On 8th April, WordPress closed this plugin on its repository of plugins. It is now not available for download.
According to researchers at Wordfence, “The first flaw that enables this attack is present in the yellow-pencil.php file within the plugin. The yp_remote_get_first() function is called on every page load and checks if a specific request parameter (yp_remote_get) has been set. If it has, the plugin escalates privileges to that of an administrator for the remainder of the request.”
When the parameter status is checked out, the plugin enables the attackers to take actions on websites, which are usually meant to be done from administrators only.
But what is scarier is that the YellowPencil plugin hack is part of a larger campaign that is run by the same attacking group, according to researchers at Wordfence.
“Exploits so far are using a malicious script hosted on a domain, hellofromhony[.]com , which resolves to 176.123.9[.]53.”
Also read: Microsoft develops SECCON framework to strengthen security of Windows 10 devices
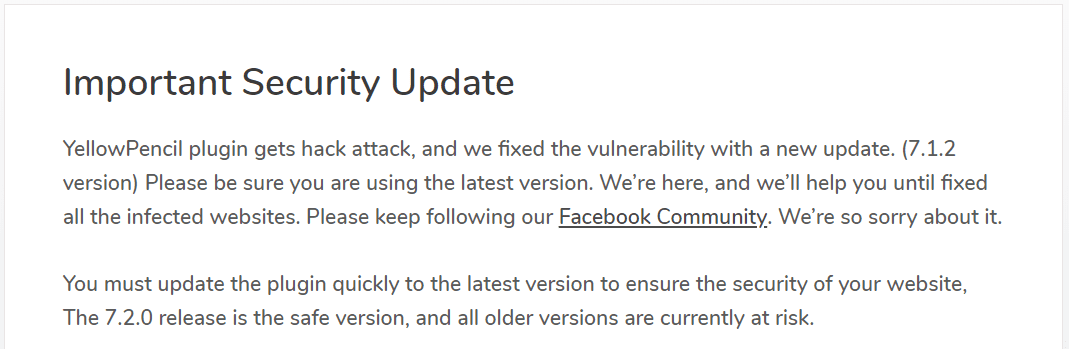
The developers behind the YellowPencil have fixed the vulnerability with a new update. To avoid the websites from getting into the hands of attackers, users must update their plugin to the latest version. All the older versions of YellowPencil are currently at risk.