Ransomware is a type of cyber threat that is very hard to get rid of. It keeps getting more and more advanced, and the latest form of it is very dangerous for organizations all over the world. This new ransomware doesn’t use new technology. Instead, it uses a new business model called Ransomware-as-a-Service (RaaS).
Ransomware-as-a-Service (RaaS) is an arrangement between two people. First is an operator, who develops and maintains the tools to power extortion operations. The second person is an affiliate, who deploys the ransomware payload. After the affiliate conducts a successful ransomware and extortion attack, both parties share the profit.
How does RaaS operate?
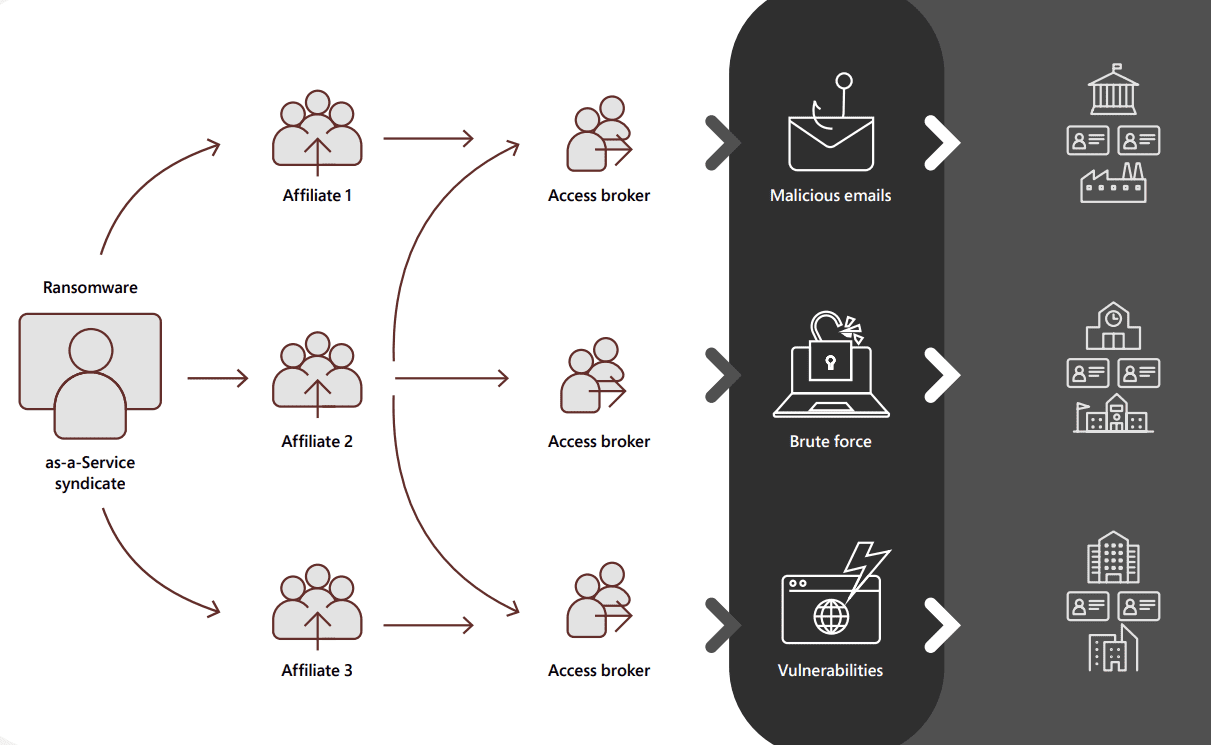
- The RaaS model makes it easier for criminals who don’t have the skill or ability to make their tools to do attacks. They can just buy network access from someone else who has already broken into a system.
- Many RaaS programs offer a suite of extortion support services like leak site hosting and integration into ransom notes, decryption negotiation, payment pressure, and cryptocurrency transaction services.
- RaaS operators provide value to their affiliates by giving access to compromised networks. Access brokers scan the internet for vulnerable systems that can be compromised and reserved for later profit. Compromised credentials are so important to attackers as in many instances, the price includes a guaranteed administrator account.
- One factor that makes the threat of RaaS so concerning is that it relies on human attackers who can make informed and calculated decisions and vary attack patterns depending on what they find in the networks where they land.
- Attackers use their skills and knowledge to try to defeat the security products in an environment during the hands-on-keyboard phase of an attack.
Microsoft uses the term human-operated ransomware to define such attacks as a chain of activity that culminates in a ransomware payload and not as a set of malware payloads to be blocked.
How can organizations protect themselves from Ransomware-as-a-Service?
Build credential hygiene and audit credential exposure:
Develop a logical network segmentation depending on privileges that can be applied alongside network segmentation for limiting lateral movement. Auditing credential exposure is critical to prevent ransomware attacks and cybercrime in general. IT security teams and SOCs should work together to reduce the number of people with administrative privileges, and also understand how exposed their credentials are.
Harden the cloud and internet-facing assets:
Security teams should focus on making sure the security identity infrastructure is strong. This includes making sure that all accounts have multifactor authentication (MFA), and that cloud admins/tenant admins are treated with the same level of security and credential hygiene as Domain Admins. To reduce exposure, organizations can use the threat and vulnerability management capabilities in endpoint detection and response products to find and fix vulnerabilities.
Close security blind spots:
Organizations should make sure that their security tools are running in the best way possible and that they perform regular scans of the network to make sure that all systems are being protected by the security tools.
Reduce the attack surface:
To prevent ransomware attacks, set rules to reduce the surface that attackers can use to launch their attacks. It was observed that organizations that had clearly defined rules were able to mitigate the attacks in their early stages before any damage was done.
Evaluate the perimeter:
Organizations must identify and secure perimeter systems that attackers might use to get into the network. Public scanning interfaces like RiskIQ can be used for augmenting data.
Prepare for recovery:
If your business is hit by ransomware, you should have a plan to recover quickly. This will be cheaper than paying the ransom. Make sure you back up your critical systems regularly and protect those backups against being deleted or encrypted. Try storing backups in online immutable storage or fully offline or off-site.
The ransomware business model is evolving and becoming more dangerous as we speak. However, some things can be done to protect organizations from ransomware attacks. By following the points outlined in this blog post, you can make it much harder for ransomware operators to succeed.
Image and source credits: Microsoft
Read next: Government websites among those leaving Git files vulnerable to attack








