Is your organization at risk of a cyberattack? The answer is yes- your organization can face cyber attack, anytime. There are a number of applications used by organizations today and as per a research by Synopsys titled 2021 Software Vulnerability Snapshot, almost all, 97% of applications have some form of vulnerability.
In this research, 3,900 tests were conducted on 2,600 target applications or systems. The research company performed tests for its customers – both, with access and without access to applications.
Following are the key highlights from the research:
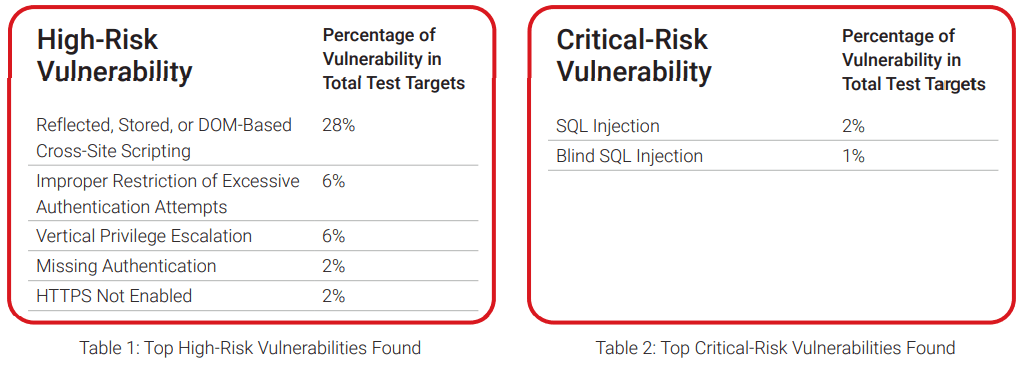
- Vulnerabilities and Security Issues: 30% of the vulnerabilities were found to be high-risk vulnerabilities such as cross-site scripting (XSS) and 6% were critical-risk vulnerabilities, including remote code execution and SQL injection vulnerabilities.The research revealed that the most critical-risk vulnerabilities are caused by SQL injection in which bad actors become capable of inserting SQL commands into the application interface to manipulate back-end databases.

Further, it concludes that easy availability of exploitation tools help hackers in accessing sensitive information. - Vulnerabilities Breakdown: The vulnerabilities found in research closely matched with the OWASP’s top 10 vulnerabilities in 2021. These were discovered in 76% of the targets. Out of the overall vulnerabilities, 19% matched with OWASPs A01:2021—Broken Access Control category. Server Misconfiguration stood at 21% of the total vulnerabilities found in the report closely related with OWASP A05:2021—Security Misconfiguration category.

- Data Storage and Communication Vulnerabilities: During mobile tests, it was found that 80% out of the total vulnerabilities were associated with insecure data storage. And more than 50% were related to vulnerable communications. These vulnerabilities allow hackers to gain unauthorized access to a mobile device via malware.
- Lower-Risk Vulnerabilities: More than 60% of the total vulnerabilities were Low to Medium risk, meaning, the vulnerabilities were not exploitable by attackers. Yet, these were exploitable to facilitate attacks. For example, Low-risk vulnerabilities such as verbose server banners found in around 50% of the tests contained critical information and could provide important details to the hackers, such as server type, name, or server version – which can allow hackers to attack specific technology stacks.
The report has also made a few recommendations to help organizations minimize security risks and avoid cyber-attacks. It advises businesses to draft security policies and implement them in order to protect themselves against cyberattacks as in most of the vulnerabilities found, 77% were due to missing or inadequate company policies.
Another recommendation is a software bill to detail third-party libraries which are used in software applications. If infected, these libraries can make it difficult to gather information or track the system. According to the report, nearly one in five tests revealed software applications using infected or vulnerable libraries by third-party.
Cybersecurity risks are growing in complexity but understanding them and taking the right measures is the best way to protect your networks and systems.
Source: Synopsys
Read Next: Increasing Interest in Talent Acquisition for Cybersecurity and 5 Tips to Hunt One