As organizations increasingly adopt hybrid work models, the dynamics of cloud security are rapidly evolving, and the complexity of application security is on the rise. With the evolution of cloud-native application development and the changing cloud infrastructure, the responsibility for security is shared between cloud service providers and their customers.
However, responsibility for customers’ applications, data, and access management falls solely on the organizations’ security and development teams, who must collaborate to secure their cloud environments. The top challenges faced by organizations in providing cloud security are:
- Managing overall security across teams
- Including security in the cloud-native development lifecycle
- Training employees to use security tools
- Reduced visibility into security vulnerabilities across cloud resources
- Determining the correct tools to address security needs
In light of these challenges, it is essential to understand how organizations are selecting and operationalizing their security tools and which practices are proving effective.
The Palo Alto survey on the state of cloud-native security answers these questions and others to equip teams with the resources they need to succeed in securing their cloud environments. Read on to know.
How are enterprises approaching cloud security?
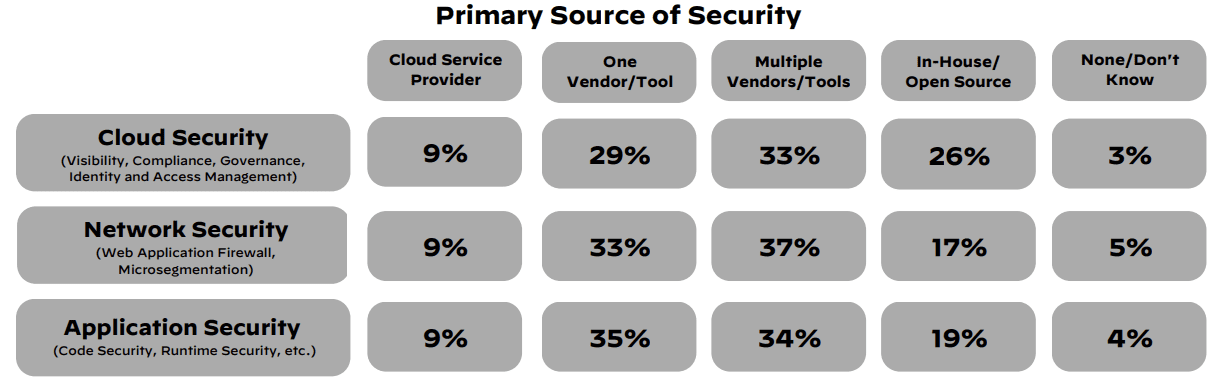
Enterprises adopt either a single or multiple security vendor/tool approach to secure their clouds, networks, data, and applications.
When evaluating security solutions, organizations prioritize best-in-class capabilities and ease of use. It’s worth noting that pricing also plays a crucial role in their decision-making process. This is because cloud security expenditures often exceed expectations for over half of businesses.
In-house and open-source tools were utilized by 25% of respondents for cloud security, whereas this approach was less common for network security (17%) and application security (19%).
Surprisingly, 9% of respondents still primarily rely on their cloud service provider to ensure cloud security measures are in place across their environment.
Even after deploying multiple security tools, enterprises still face significant security incidents, with gaps in response efficacy and efficiency. Only a small fraction of respondents (about 10%) can detect, contain, and resolve threats in under an hour.
The survey found that 39% of respondents experienced an increased number of breaches, and over 30% reported more intrusion attempts and unplanned downtime. Additionally, 68% of organizations are unable to detect a security incident in less than an hour, and once detected, 69% cannot respond to the threat in under an hour.
Overall, security incidents are becoming harder to detect and contain.
How are application developers shaping cloud security?
A majority (80%) of those surveyed acknowledged that developers have a clear understanding of their security responsibilities throughout the development lifecycle. Additionally, 80% of respondents stated that security professionals are integrated into their development and operations teams, particularly during the design phase.
Respondents with cloud security teams of over 30 members reduced from 54% in 2022 to just 16% this year, while 58% reported having teams with less than 20 members. This decline could be due to several factors such as hiring challenges, the belief that fewer team members are needed after significant cloud investment, and outsourcing security tasks to MSSPs.
However, there is greater collaboration between application developers and security tools/teams, particularly during the design phase.
Developers are willing to use tools and procedures to build secure applications, but they have a threshold for how much shift-left responsibility they can and want to undertake. Like security professionals, stress seems to be affecting them as well. Therefore, it is essential to seamlessly integrate user-friendly security tools and teams into the DevOps workflow to minimize security roadblocks for application teams.
Actions enterprises must take for ensuring cloud-native security
- Embed security in the early stages of application development
To minimize risks in production, it’s essential to detect and prevent security issues in the early stages of application development. Security teams should have a thorough understanding of the organization’s coding, building, deployment, and cloud operations. They can then identify the least disruptive insertion points for security in the CI/CD pipeline.
A good starting point is to raise visibility and recommend fixes for software with known vulnerabilities and container image scanning. This helps to gain early buy-in from DevOps or platform teams and integrate security seamlessly into the development process.
- Implement continuous cloud visibility for real-time insights
To make cloud security and compliance more manageable, it is crucial to remove any blind spots. This can be achieved by implementing continuous cloud visibility, which involves detecting cloud assets, misconfigurations, and vulnerabilities, as well as anomalous or suspicious behaviors that may indicate a security breach.
Continuous visibility provides security teams with real-time insight into their organization’s cloud environments, enabling them to quickly identify and respond to any security incidents. This level of visibility allows security teams to answer critical questions, such as who, what, when, and where, for any activity within their cloud environments.
- Embrace threat prevention strategies
While it’s crucial to address misconfigurations and known vulnerabilities, these measures alone can’t fully protect against insider threats or undetected breaches. To mitigate these risks, organizations should adopt threat prevention techniques that actively block zero-day attacks and contain lateral movement in the event of a breach. Additionally, these techniques can provide compensating controls when developers can’t patch known application vulnerabilities.
To ensure best practices for least-privilege access for your users, consider using preventative techniques such as calculating net-effective permissions across your cloud resources. At a minimum, organizations should apply prevention solutions to their mission-critical applications.
- Align cybersecurity tactics with cloud migrations
To avoid security becoming a barrier during cloud migrations and expansions, it’s essential to think ahead. Many organizations make the mistake of adopting new security technologies for each new use case, which leads to a proliferation of isolated tools that impede cloud security teams and result in blind spots.
To address this issue, organizations should review their cloud adoption objectives for the next 2-5 years, such as containerization, serverless, APIs, CI/CD pipelines, and open-source tools, and adopt solutions that meet current and future priorities.
- Consider consolidating security tools
Taking a platform approach to unifying data and security controls can be a powerful solution. While individual tools may address important use cases, they do not offer a comprehensive risk view. By consolidating security tools, security teams can automate correlation and address critical security issues across the application lifecycle.
Source: Palo Alto Networks
Read next: NTT’s new Managed Detection and Response service takes cyber resilience to the next level








