A new ransomware gang, Black Basta, has risen to prominence after breaking into the networks of at least 50 firms across industries, in just a few months. The Black Basta attacks have resulted in multi-million dollar crimes, launching double-extortion attacks around the world. The ransomware moves too fast to cause symptoms that alert defenders to any potential compromise or infection.
Black Basta mode of operation
The Black Basta ransomware is finding its entry through phishing, social engineering tactics, and similar forms of disguise to carry out successful exploitations.
- Infectious files come in formats like archives, executables, Microsoft Office and PDF documents, JavaScript, and so on. Opening such a file starts the infection process.
- It can also enter your system stealthily via deceptive downloads from untrustworthy download channels.
- Other common distribution methods include malicious attachments/links in spam emails and messages, online ad scams, cracked software, and programs on malicious sites.
Black Basta requires admin rights to run, else it shows a message in the command prompt, as shown below.
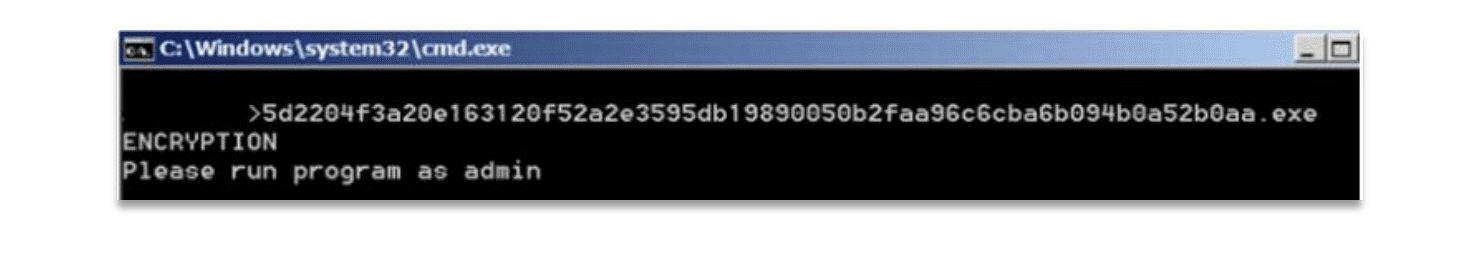
After the ransomware is run, it removes the shadow copies, disables Windows recovery and repair, and boots the PC in safe mode.
It also drops the files %Temp%\fkdjsadasd.ico and %Temp%\dlaksjdoiwq.jpg to change the desktop wallpaper and icons for encrypted files. It first changes the desktop wallpaper and then boots the infected device into safe mode.
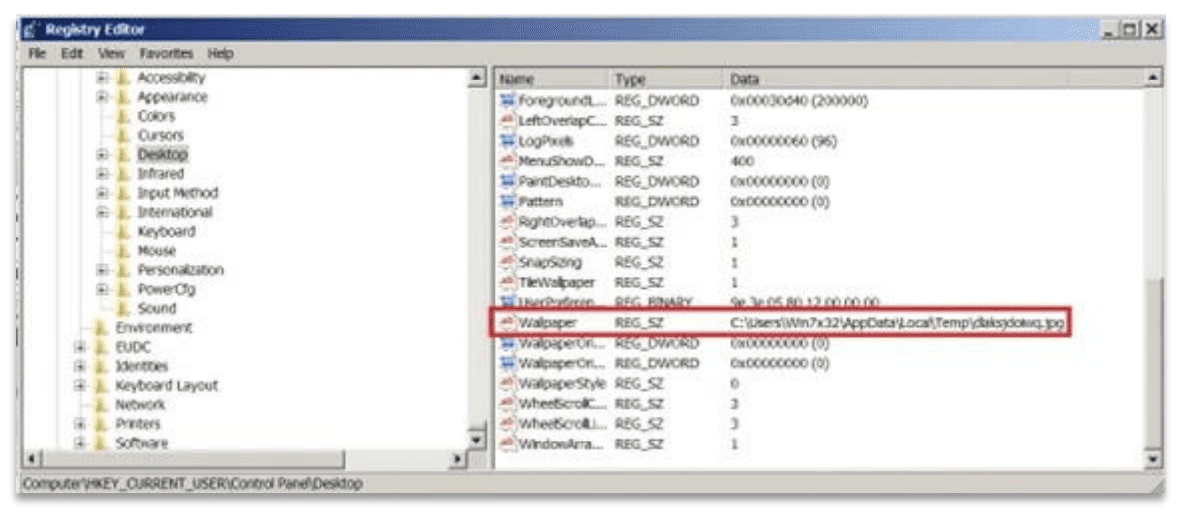
The registry entry created after Black Basta ransomware changes the wallpaper on the infected machine.
Once the desktop wallpaper is changed, it adds registry keys to change the icon of the encrypted files with the .basta extension. Then it encrypts files while the device is in safe mode and appends all encrypted files with the .basta extension.
Infected files with .basta extension
The ransom note will also be present in all the folders affected by the ransomware.
Black Basta employs a double extortion scheme which includes exfiltrating confidential data before encryption and threatening victims with the public release of the stolen data.
Are there ransomware groups working together?
Several emerging threat groups are working together to carry out successful attacks. This is creating difficulties for cybersecurity experts to mitigate threats at an early stage. It has been observed that the Black Basta ransomware group has joined hands with QBot for gaining initial access to corporate environments. A few researchers were also doubtful that Black Basta could be a rebrand of Conti as there were multiple similarities between them from leak sites and payment sites to victim recovery portals. Conti has however denied this.
Recommendations
Organizations must establish security frameworks that distribute resources systematically for establishing a strong defense strategy against ransomware. Some best practices that can be considered are:
- Taking inventory of assets and data, auditing event and incident logs and identifying authorized and unauthorized devices and software
- Granting admin privileges and access only when it is necessary to an employee’s role.
- Monitoring network ports, protocols, and services and activating security configurations on network infrastructure devices like firewalls and routers
- Establishing a software allow list that only executes legitimate applications
- Conducting regular vulnerability assessments and performing patching or virtual patching for operating systems and applications.
- Keeping software and applications updated to their latest versions
- Implementing data protection, backup, and recovery measures and enabling multifactor authentication (MFA).
- Using advanced detection technologies powered by AI and machine learning to detect early signs of attack.
- Regularly training and assessing security skills of employees.
- Conducting red-team exercises and penetration tests.
Read next: Endpoint security market to grow over $19.8 billion by 2025








