According to the 2023 Data Protection Trends Report by Veeam, a staggering 85% of organizations faced at least one cyberattack in the past year, marking a notable increase from the 76% reported in the previous year. Veeam conducted a survey among IT leaders especially security professionals, CISOs, IT operation generalists and backup administrators from organizations that encountered at least one ransomware attack in 2022. The purpose was to assess the effects of ransomware attack on their systems, as well as to gain insights into their future IT strategies and data protection initiatives. This latest Ransomware Trends Report highlights the following key discoveries.
Clean and recoverable backups are key for cyber preparedness
87% of organizations have a risk management program in place that drives their security roadmap or strategy. However, only 35% of organizations believe that their program is functioning effectively, while 52% are actively seeking ways to enhance their situation. Surprisingly, the remaining 13% do not have an established risk management program at all.
Irrespective of the name given to the program or team responsible for planning against cyber events, the most common elements of the playbook for preparing against an attack are as follows:
- Clean backup copies: This includes ensuring the existence of data that is resilient against attacks and does not contain any malicious code.
- Recurring verification of recoverable backups: Regular checks are performed to confirm that the backups are indeed recoverable and can be relied upon in the event of an attack.
Insurance payments for ransomware attack pose challenges
The report also highlights the reliance on insurance for ransom payments, with 77% of ransoms being paid through insurance channels. However, this avenue is becoming increasingly difficult and expensive.
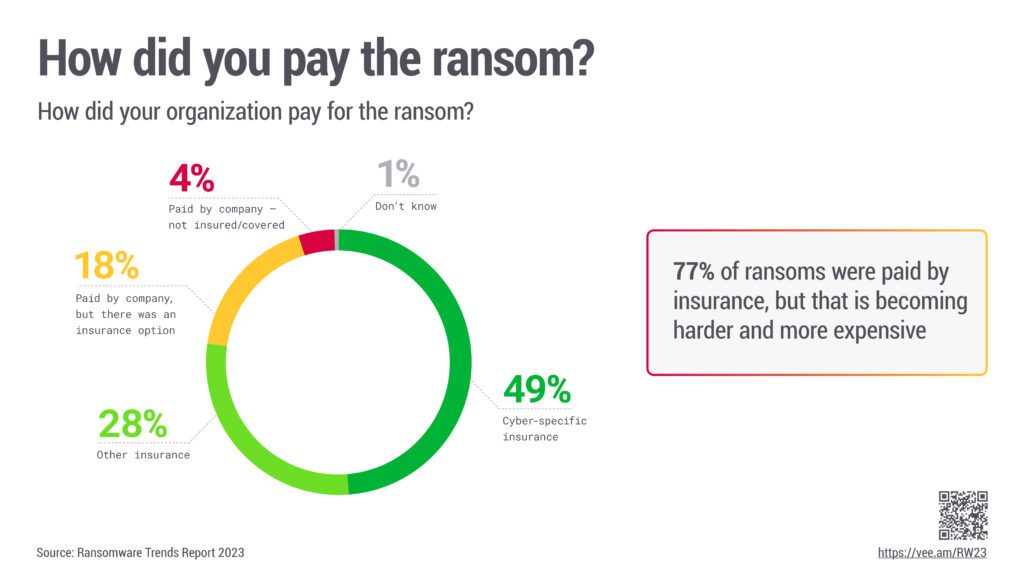
Although the ideal response would be to avoid paying ransoms by recovering the data, only 16% of organizations surveyed chose this approach, a slight decrease from the 19% reported in the previous year.
Backup repository vulnerabilities hamper recovery efforts
Alarming findings reveal that even among the 80% of respondents who acknowledged paying the ransom, 25% of them were unable to recover their data despite meeting the demands. Two primary reasons attributed to these failures include:
- payment via insurance instead of by the organization itself, and
- the compromised state of backup repositories rendering recovery impossible.
Shockingly, the cyber attackers managed to affect backup repositories in 75% of the attacks.

Immutability and air gapping key to successful recovery
Only a small fraction, 16%, were able to successfully recover their data without paying the ransom. This required having recoverable data stored within repositories. Less than a quarter of the victims stated that their backup repositories remained unaffected by the attackers.

To achieve this level of resilience, organizations need to implement immutability or air gapping measures to safeguard backup repositories from malicious manipulation. Remarkably, a minimal 2% of companies disclosed a lack of immutability in any level of their backup solution in 2023. A considerable number of organizations proudly showcased immutability or air gaps implemented across multiple tiers.
In 2023, it is possible for backup data to maintain its immutability throughout the entire data protection lifecycle, spanning short-term disk storage, resilient BC/DR clouds, and long-term tape storage.
Cloud infrastructure emerges as preferred recovery site
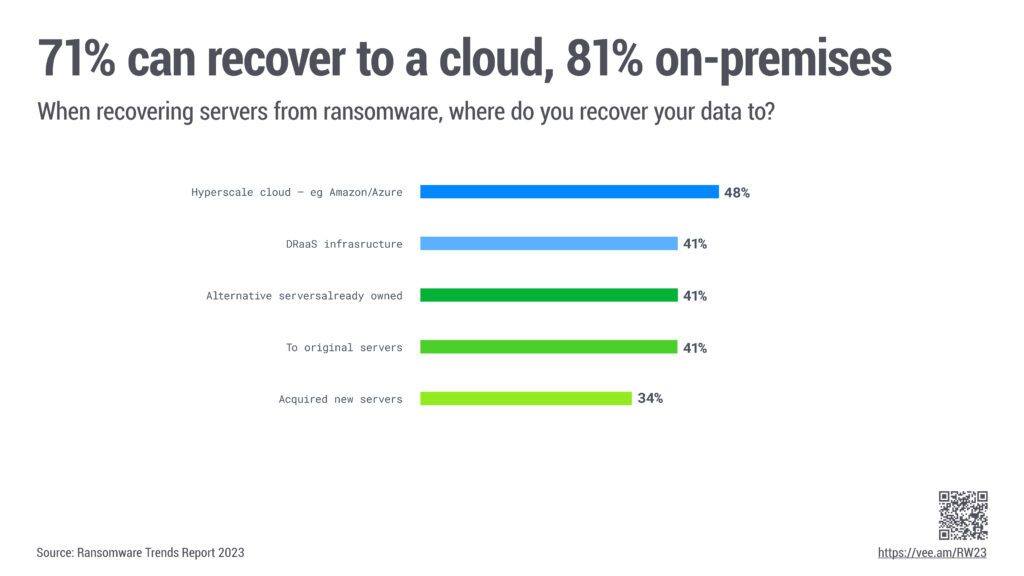
For IT professionals, selecting the recovery destination is a pivotal choice when implementing BC/DR (Business Continuity/Disaster Recovery) strategies, and factors such as cloud-based solutions and datacenter infrastructure play a crucial role. According to the 2023 report, cloud-hosted infrastructure emerges as the top choice for ransomware recovery on a considerable scale, closely followed by managed disaster recovery as-a-service (DRaaS) platforms. This trend aligns with the significant number of organizations intending to utilize cloud repositories as their immutable recovery sources.
Organizations embrace flexible recovery plans
Most organizations demonstrate flexibility in their recovery plans. Approximately 19% exclusively plan to recover to the cloud, while 29% solely intend to recover to on-premises servers. A significant proportion, 52%, have developed plans that incorporate both cloud and on-premises recovery options, reflecting a balanced approach to data protection and disaster recovery in the face of cyber threats.
Wrapping up – The latest ransomware trends indicate that the likelihood of being a victim of a ransomware attack is not just possible but highly probable. On average, organizations can expect to lose around 15% of their production data with each attack. This has led to increased investments and prioritization of ransomware prevention, as well as improved remediation processes and technologies. In essence, having a secure backup is the only viable alternative to paying the ransom.
Based on insights gained from past attack experiences, organizations now employ key technologies to prepare for future assaults. These include,
- implementing immutable storage in disks and clouds
- utilizing air-gapped media for data protection
- conducting staged restorations to prevent re-infection during recovery
- adopting hybrid IT architectures to facilitate server recovery on alternative platforms
Source credits: Ransomware Trends 2023 Report
Read next: New dangerous ransomware group is on the rise: How can you protect your business?








