As businesses have shifted to remote and hybrid models, the need for cybersecurity has become more critical than ever before. With employees operating from multiple locations and devices and connecting to multiple networks, organizations face new and evolving threats that they must be prepared to defend against. In response to these challenges, Cisco has developed the Cybersecurity Readiness Index, which seeks to measure the readiness of organizations around the world to meet these modern security challenges. In this article, we will explore the state of cybersecurity readiness in today’s business environment.
The index reveals that only 15% of organizations worldwide possess a mature level of cyber readiness to effectively manage the security risks of the current hybrid world. Failing to adequately prepare could lead to severe consequences. As many as 60% of survey respondents reported experiencing a cybersecurity incident in the last 12 months.
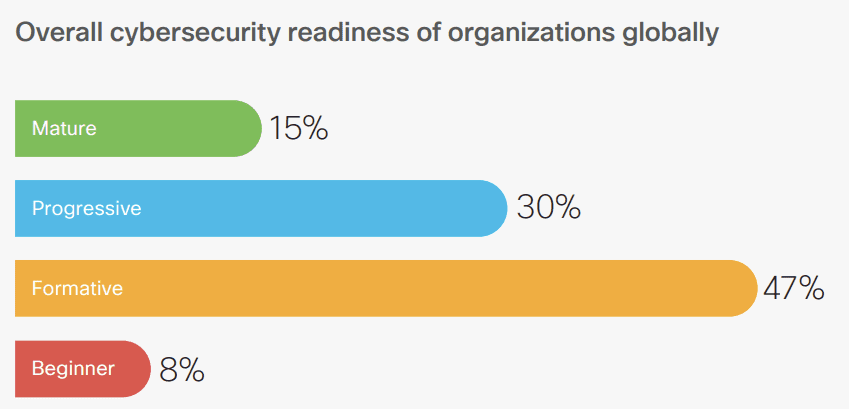
The gap between cybersecurity resilience and the potential threats is alarming and urgent action is required from global business and security leaders to address this issue before it widens further.
Identity protection readiness
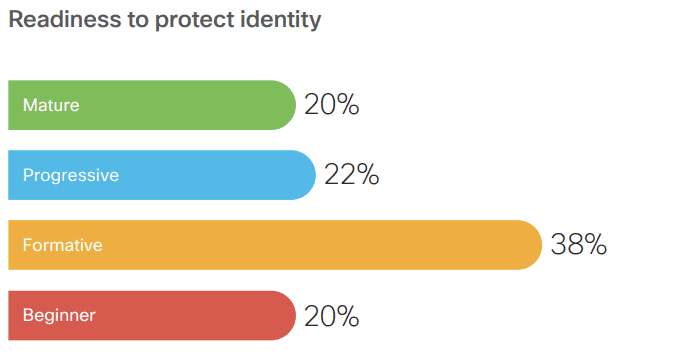
- In hybrid working, traditional perimeter security is inadequate as data is spread across multiple services, devices, applications, and users.
- Identity management is the number one risk for cyberattacks, according to 24% of respondents, as per the survey.
- Integrated Identity and Access Management (IAM) solutions, such as Multifactor Authentication, are being added as a second layer of verification for users.
- 95% of companies have implemented some form of identity management solution, with IAM being the most popular.
- Privileged Access Management is also being added as an additional layer of security to identity management by some companies.
- However, of companies that have not yet implemented identity solutions, 69% have no intention to do so.
- For companies that plan to implement identity solutions, it may take up to five years to complete their implementation.
Device protection readiness
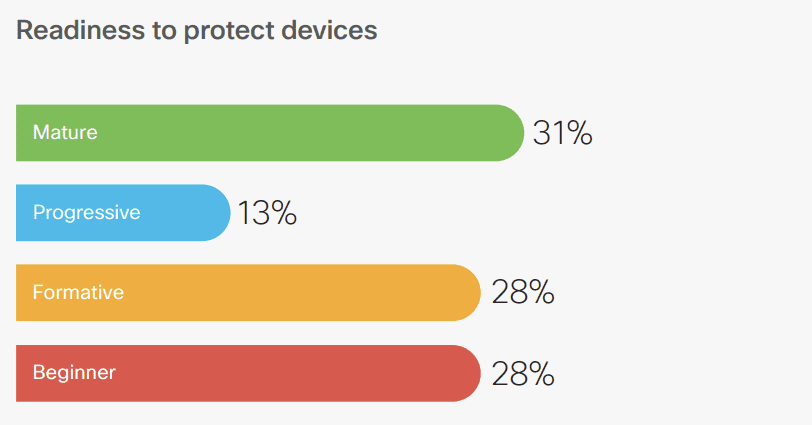
- The need for remote access to data has led to a rise in the number of devices used by employees.
- 73% of respondents use enhanced anti-virus solutions to protect devices, while 65% have built protections into the operating system using host controls.
- Endpoint protection platforms are the third most popular solution.
- Despite a high number of companies claiming to have these solutions, 56% are at the beginning of their implementation journey.
- Device management does not seem to be a high priority for those who have not yet implemented these solutions, with two-thirds stating they have no plans to do so.
Network protection readiness
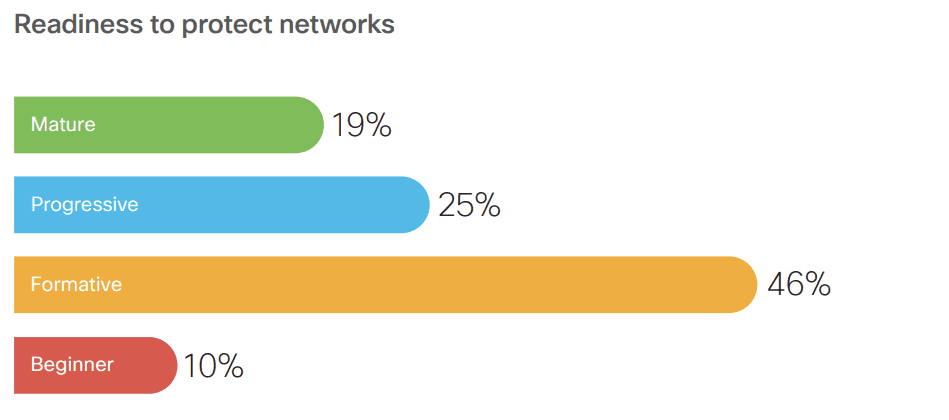
- Network protection ranks second in the list of top five priorities for companies.
- 69% of companies use firewalls with built-in Intrusion Prevention Systems (IPS) for network protection.
- Network segmentation policies based on identity and Network Behavior Anomaly detection tools (60%) are also popular solutions.
- The scale of deployment of network protection solutions is not keeping pace.
- Only 19% of companies sit in the Mature category of network security readiness, while most are either in the Formative or Beginner category.
- Companies need to consider novel approaches such as Secure Access Service Edge (SASE) to keep up with dynamic business models and hybrid work.
Application workload protection readiness
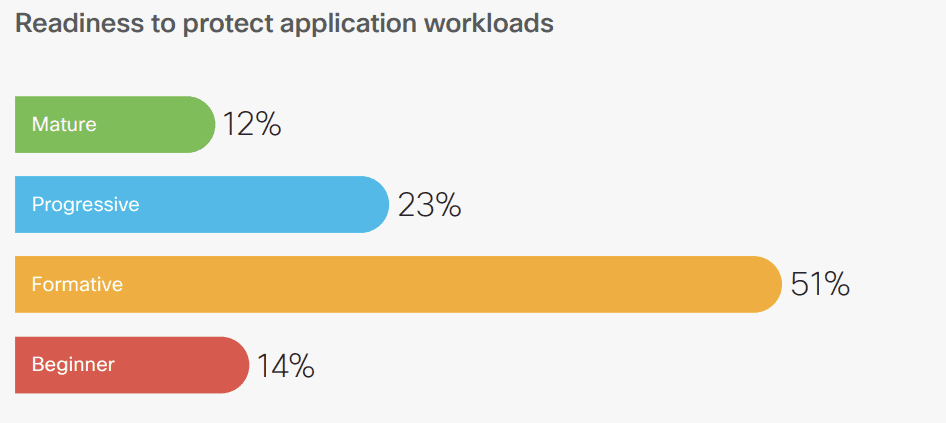
- Businesses have rapidly come to heavily rely on applications in the past couple of years.
- 97% of organizations have deployed some kind of solution to protect application workloads.
- 66% use host software firewalls, 64% have opted for endpoint protection, and 34% are using DLP solutions.
- Host software firewalls are the number one choice for most firms but only 67% of them have fully deployed the solution.
- 88% of respondents plan to deploy application protection solutions within 24 months, however, 12% expect it will take three to five years due to budgetary constraints.
Data protection readiness
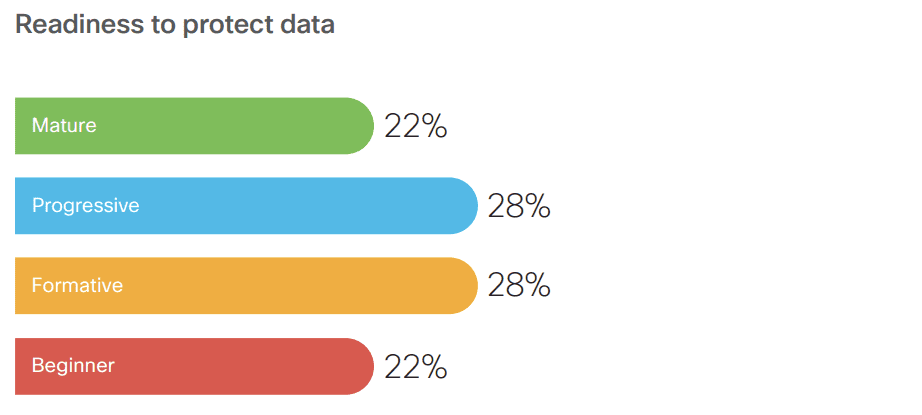
- Organizations understand the importance of data protection and have solutions in place to protect it, such as encryption tools, backup and recovery tools, identification and classification with data leak protection (DLP), and host IPS and protection tools.
- 94% have fully or partially deployed encryption tools while 92% have either completed or are on the road to completing the rollout of backup and recovery tools.
- 55% have deployed identification and classification with DLP, while 61% have deployed host IPS and protection tools.
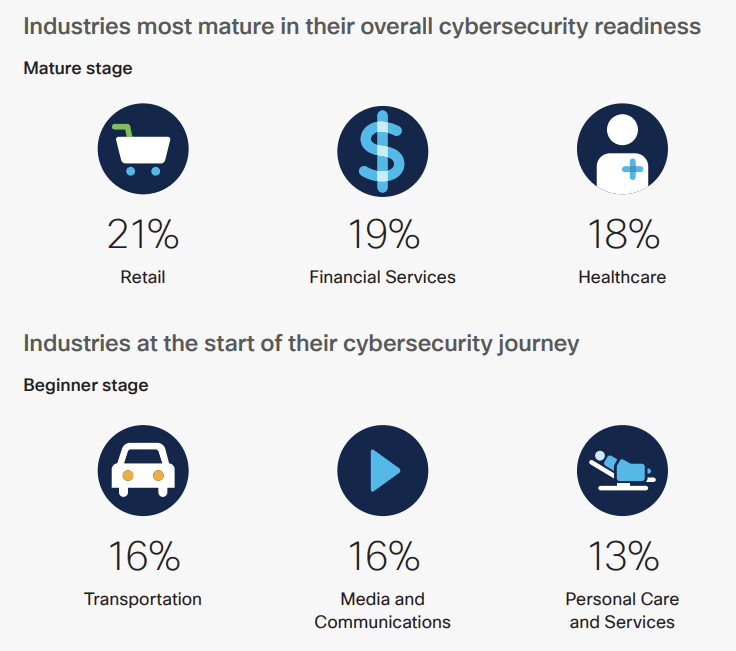
The retail industry has the most cybersecurity readiness with 21% of organizations falling in the mature category
The industries that are best prepared to tackle cybersecurity challenges are those with the most to lose and gain from keeping threats at bay. According to the research, the retail sector has the highest number of organizations (21%) in the most advanced state of readiness, followed by financial services (19%) and healthcare (18%), which face the immense challenge of securing patient records.
Smaller organizations face a significant challenge in achieving security readiness, with 32% in the Beginner category for device protection, compared to 27% in the Mature category. This disparity can be attributed to the wide range of companies of this size, including family businesses, tech startups, and professional services firms, each with varying levels of expertise. With small and medium-sized enterprises accounting for about 90% of businesses worldwide and more than 50% of employment, there is a pressing need to provide more support to help them improve their security readiness.
The current business landscape demands a proactive approach to protect critical assets from cyber threats. Enterprises must focus on safeguarding their identities, devices, network, data, and applications to mitigate risks. These five pillars of security must work in harmony to ensure a cohesive and robust security posture. Failure to do so can make organizations vulnerable to cybercriminals, risking reputational damage, financial loss, and regulatory penalties. As threats continue to evolve and intensify, companies must prioritize security and adopt advanced security solutions to stay ahead of the curve.
Image and source credits: Cisco Cybersecurity Readiness Index
Read next: 60% of organizations currently use mixed IT Infrastructure, reveals Nutanix








