Malicious actors are leveraging GitHub Actions (GHA) and Azure virtual machines (VMs) for cloud-based cryptocurrency mining. The attackers can abuse the runners or servers provided by GitHub to run an organization’s pipelines and automation by maliciously downloading and installing their cryptocurrency miners to gain profit easily. The different GHA YAML scripts found on GitHub tried to mine all kinds of cryptocurrency by using the GHA runners.
Malicious actors have been targeting the cloud environment for cryptocurrency mining activities and cybercriminals compromise cloud infrastructure for less lucrative CPU-based cryptocurrency-mining operations. While this malicious activity has been there for a while, the frequency of these attacks is increasing at the same rate at which new cloud services are created and offered for free.
Cryptocurrency miners abusing Linux and Windows runners
Azure Standard_DS2_v2 virtual machines host both Linux and Windows runners and have two vCPUs and 7 GB of memory each. Cryptocurrency miners follow a similar approach to abuse the Linux runners that cybercriminals use for exploiting Windows runners to operate their mining scripts. They are continuously trying to dodge detection by GitHub to prevent their actions from getting disabled. GitHub provides the runner, a server designed to run workflows (actions of malicious actors). The workflows are deployed on Azure and are terminated once an enterprise’s automation is completed. Users need not pay for this service even with a free GitHub account.
Japanese IT security company – Trend Micro, has identified more than a thousand repositories and over 550 code samples that abuse GitHub Actions for cryptocurrency mining by leveraging the runners provided by GitHub. The following figure shows GitHub search results from cryptocurrency miners using GHA.
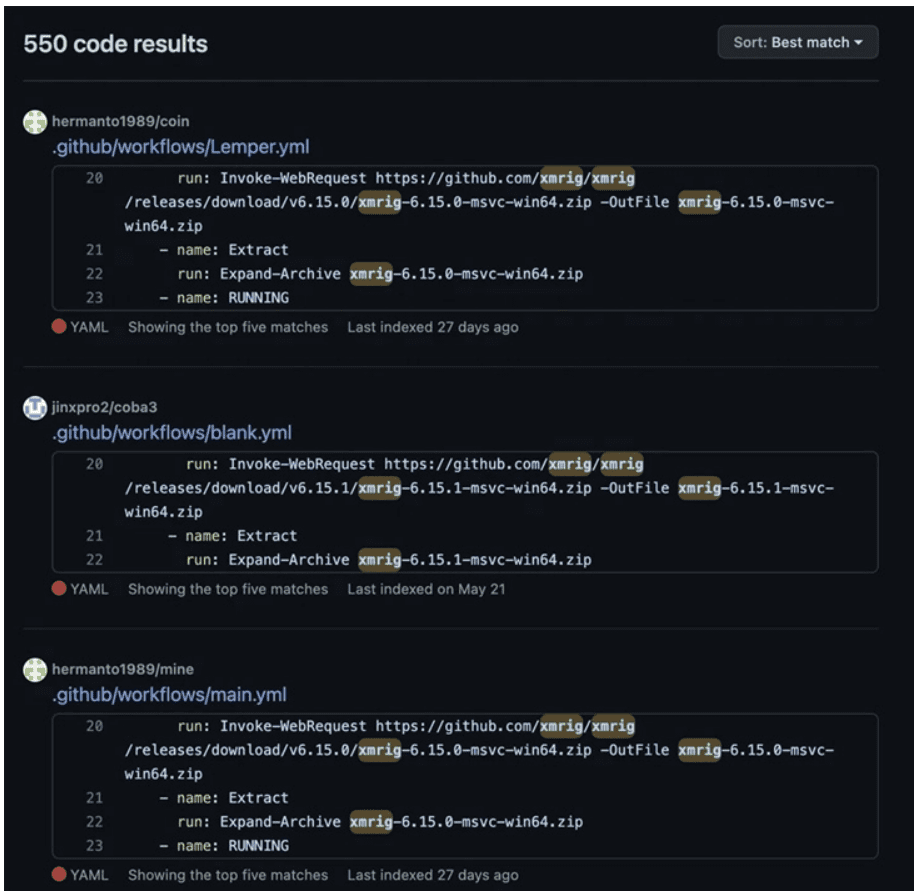
“For as long as the malicious actors only use their accounts and repositories, end-users should have no cause for worry. This is a problem GitHub is cognizant of and is trying to address and mitigate as much as possible. However, it is hard to eliminate the problem. Problems arise when these GHAs are shared on GitHub Marketplace or used as a dependency for other Actions,” shared Trend Micro in its post.
How can you detect cryptocurrency miners?
Even a few minutes or hours of a compromised network can generate significant profits for malicious actors. Therefore, both Cloud service providers (CSPs) and customers must be aware of these attacks and be able to identify and prevent them in their environments.
Increased resource consumption can be cited as the first indicator of possible cryptocurrency mining exploits. Resource consumption spikes CPU utilization to 100%, slowing down workloads or applications that are running. There is also a possibility of these workloads stop working due to high CPU usage. Customers and CSPs must look out for such instances to identify occurrences of cryptocurrency mining. 100% CPU utilization can increase the costs by up to 600% with on-demand pricing and this can scale and increase quickly based on the number of compromised workloads for cryptocurrency mining. Therefore, any sudden increase in the cloud monthly expenses should be looked into carefully.
Read next: The 8220 gang updates malware targeting Linux systems








