LocalBlox, a data search service provider who automatically crawls, discovers, extracts, indexes, maps and augments data in a variety of formats from the web and from exchange networks, has been found to expose around 48 million records of personal information gathered from multiple sources, including social media platforms like Facebook, LinkedIn, Twitter etc.
Discovered by the security firm UpGuard, the data was exposed via a misconfigured Amazon Web Services S3 storage instance.
The exposed data included names, physical addresses, dates of birth, personal internet usage like LinkedIn and Facebook histories, as well as Twitter feeds.
As UpGuard explained in a blog post, the exposed data “begins to build a three-dimensional picture of every individual affected— who they are, what they talk about, what they like, even what they do for a living— in essence a blueprint from which to create targeted persuasive content, like advertising or political campaigning.”
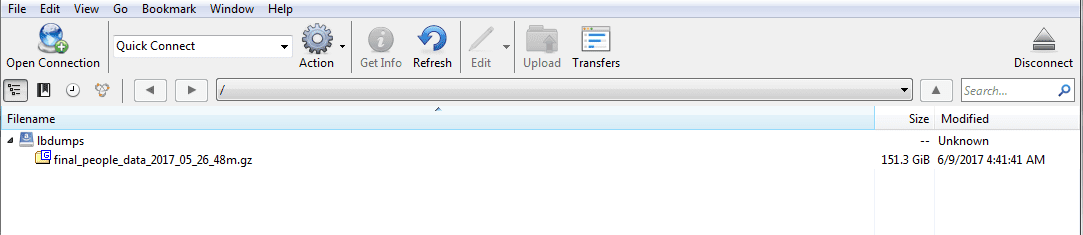
UpGuard Cyber Risk Team discovered the exposed data on 18th February when they found an AWS S3 bucket located at subdomain “lbdumps”. This bucket contained 151.3 GB compressed file, which was publicly downloadable and configured for access via the internet.
The file, named “final_people_data_2017_5_26_48m.json” contained 48 million records in json format, separated by new lines. Metadata in a header file revealed LocalBlox as the owner of file.
“The database appears to work by tracking an IP address, matching collected data to that IP address when able, and thus providing a clearer image of the behavior and background of the user at that IP address,” wrote UpGuard.
The personal data of individuals could have been held by unknown third-parties to monetize the information. It could have been used illegitimately for social engineering scams like phishing.
Also read: 25% of businesses had their data stolen from public cloud: McAfee Study
UpGuard Cyber Risk Team notified LocalBlox about the exposure on 28th February, and the file was secured later that day.








