Google has rolled out a new tool for tracking network operations on its Google Cloud Platform (GCP) called VPC Flow Logs. The move is aimed at enabling enterprises with a deeper, real-time visibility into their networks, so that they can track the network flows and improve security and business operations.
Logging and monitoring are essential to network and security operations of an organization, because these help in identifying traffic and access patterns that could present operational or security risks.
“VPC Flow Logs allow Google’s cloud customers to track network flows all the way down to an individual virtual interface, in near-real-time,” wrote Ines Envid, Google Cloud Platform product manager, in a blog post.
VPC Flow Logs is similar to NetFlow, but Flow Logs comes with additional features. It offers network telemetry for GCP environments, using which the logs can be created within five-second intervals. Also, the network telemetry logs can be collected at various levels, from a variety of sources.
Enterprises can use VPC Flow Logs to track internal VPC traffic, flows between VPC and on-premises deployments, flows between servers and internet endpoint, as well as the flows between servers and Google services.
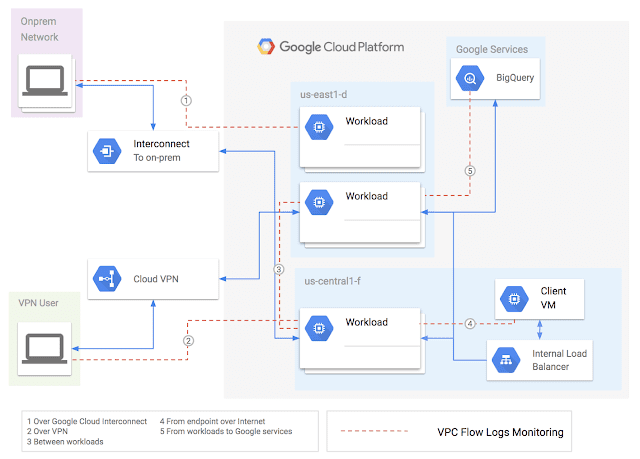
Image Source: Google
The data generated using VPC Flow Logs can be exported securely to Stackdriver Logging or BigQuery. The Stackdriver Logging enables organizations to store, search, analyze and alert on log data and events from GCP and AWS. It is a managed and scalable solution to ingest data from applications and systems from Virtual Machines.
The new tool can help companies with several operational tasks, including monitoring of applications from network perspective, and optimizing network usage and egress. It enables visibility into application’s global traffic, and allows users to optimize bandwidth utilization, network costs, load balancing and content distribution.
Also read: Google adds new features and capabilities to its TensorFlow, for AI developers
It can also help in performing network forensics to investigate suspicious behavior, and provide real-time security analysis.








