Organizations in Asia contend with familiar threats like ransomware and phishing, while also facing evolving challenges such as the growing menace of hacktivism and the transformative impact of generative AI technology. As these risks continually shift, it becomes crucial for cybersecurity teams in the Asia-Pacific (APAC) region to swiftly identify and block both established and emerging threats. Cyberint has compiled insightful data on the surge of threat techniques and goals in 2023, providing essential guidance for navigating the intricate cybersecurity landscape.
Top APAC cybersecurity threats
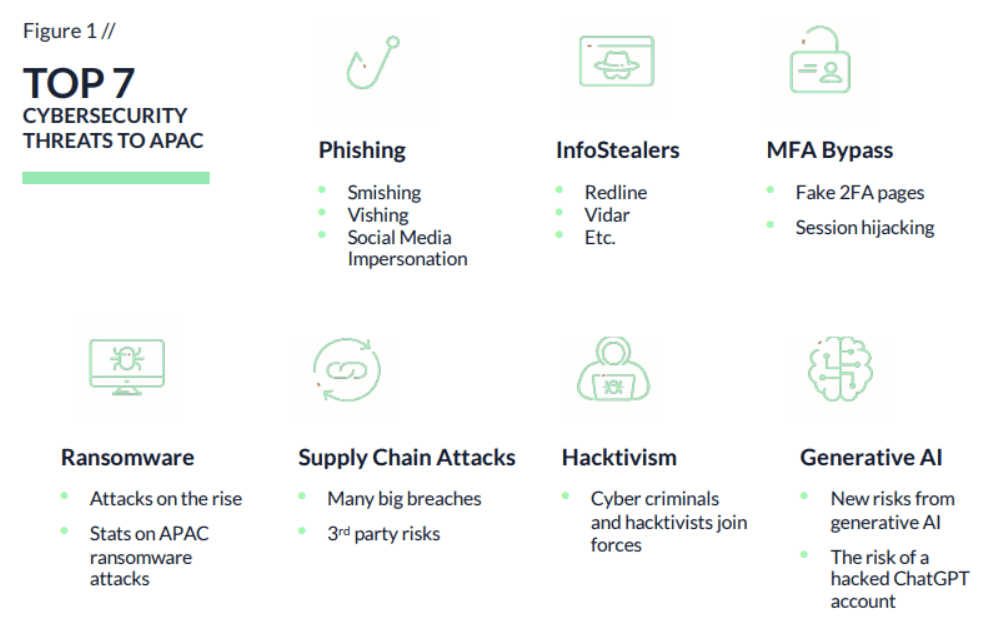
1. Phishing
Phishing attacks in Asia have experienced a remarkable surge, witnessing approximately 5 million incidents since 2022. This alarming trend is mirrored globally with a staggering 150% year-over-year increase in phishing attacks. The vectors used by threat actors include email, SMS messages (Smishing), vishing, and a novel trend of social media impersonation, notably observed in the Philippines.
Email phishing commonly uses malicious links, attachments, or reply requests to trick victims into divulging sensitive information. To counter these risks, businesses are advised to scan email systems for unusual activity and messages, emphasizing the importance of user education.
Smishing, phishing via SMS, remains a prevalent risk, underscoring the critical role of user education. Additionally, vishing, utilizing voice calls for phishing, and social media impersonations are identified as novel trends, necessitating proactive measures like user education, monitoring voice chats, and scrutinizing social platforms for signs of impersonation.
2. InfoStealers
Infostealers, a specialized form of malware existing since early 2020, are on the rise, with a notable increase in prevalence. These malicious entities operate by extracting sensitive data from compromised computers or servers and transmitting it to attackers. Prominent infostealer families, including RedLine, Aurora, Raccoon, and Vidar, are identified as significant players in this region.
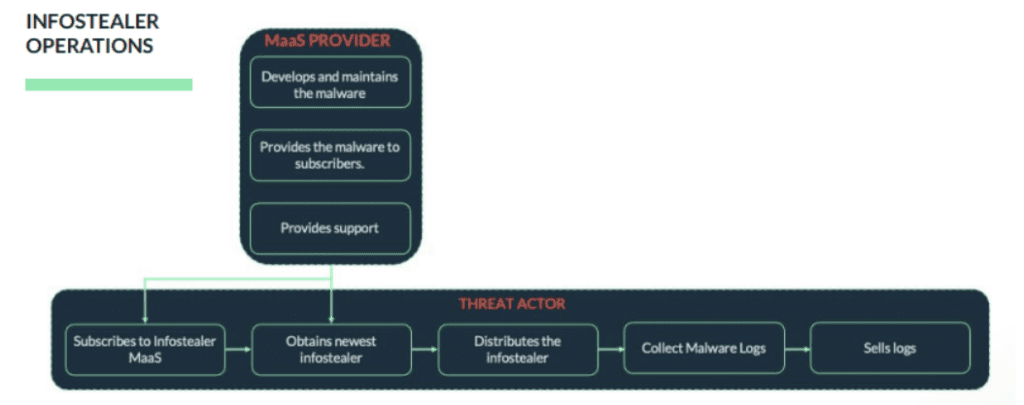
Vietnam, India, and the Philippines are highlighted as high-risk regions due to lower awareness of cybersecurity practices among their internet users. RedLine stands out as the dominant force in the APAC infostealer market, accounting for more than half of the detected activity, displaying a well-organized operational structure. Aurora and Raccoon also exhibit noteworthy presences in this malicious landscape.
3. MFA bypass
Multi-Factor Authentication (MFA) bypass in Asia is executed through two primary methods.

The first involves a real-time phishing strategy where threat actors use third-party services to identify victims, directing them to a fraudulent login portal. Once victims enter their credentials, the attacker redirects them to a fake MFA interface ultimately gaining control by obtaining the genuine MFA code entered by the victim.
The second method employs infostealers to steal website cookies, enabling attackers to store login information on their device. By planting these copied cookies, threat actors can effortlessly bypass login requirements, including MFA prompts, particularly if the app skips MFA after recent completion. These sophisticated tactics highlight the evolving landscape of cyber threats targeting MFA systems in the region.
4. Ransomware APAC cyber threats
There’s a 70% surge in ransomware incidents across Asia by the close of 2023, with Australia, India, and Japan likely topping the list due to their concentration of businesses, rendering them attractive targets for ransom-seeking threat actors. These cybercriminal groups strategically analyze countries’ financial capabilities before executing attacks.
As per the research, the frequency of ransomware attacks varies notably across industries in Asia, with professional services and engineering businesses being the most frequently targeted. In the Asia Pacific region, LockBit 3.0 is identified as the most prevalent ransomware threat, followed by ALPHV/Blackcat, underscoring the dynamic and industry-specific nature of cyber threats in the region.
5. Software supply chain attacks
Software supply chain attacks, constituting 62% of all intrusions, occur when threat actors compromise third-party software to target a company. An illustrative case is the MOVEit breach, where attackers exploited a vulnerability, affecting both paying MOVEit customers and non-customers. Such attacks pose a risk when third-party vendors have privileged access to a company’s systems or supply technology.
To safeguard against supply chain risks, it is crucial to inventory vendors to identify blind spots, and assess each supplier’s risk through evaluations of cyber hygiene. Continuous monitoring of the Deep and Dark Web is vital to detect threats like exposed credentials, malware infections, and data leaks, ensuring robust protection on an ongoing basis.
6. Hacktivism
The rise of hacktivism, involving cyberattacks in support of activist causes, poses an escalating threat in Asia and globally. The distinctions between hacktivists, cybercriminals, and nation-state actors are becoming increasingly blurred. Hacktivism-related cyberattacks are occurring worldwide, with Asia experiencing significant incidents.

Notably, a North Korean government-backed group recently orchestrated a $3 billion theft, potentially funding a weapons program. Similarly, a Chinese APT group breached trade secrets, while a Malaysian hacker group, seemingly motivated by ideology rather than official backing, targeted foreign websites in recent prominent incidents.
7. Generative AI risks
While generative AI technology offers promising possibilities, it introduces new cybersecurity challenges. Threat actors leverage genAI tools like ChatGPT to expedite their attacks, utilizing its capabilities to generate content for phishing campaigns. Furthermore, there is a concerning trend where some malicious actors are selling access to compromised ChatGPT accounts.
Beyond this, a significant risk emerges, as sensitive user data shared with generative AI services becomes vulnerable to exploitation by threat actors. Employing techniques like prompt injection, attackers can manipulate the large language model (LLM) powering genAI services, extracting users’ private data and potentially using it to facilitate subsequent attacks.
How organizations can stay safe from leading APAC cyber threats
Addressing the extensive cybersecurity threats faced by Asia-based organizations requires a comprehensive, multi-faceted strategy. This approach aims to both prevent initial targeting by threat actors and detect ongoing attacks to minimize their impact. Here is what businesses must do:
- Proper Patch Management: Identify and update outdated software promptly to prevent exploitation of vulnerabilities.
- Raise Awareness via Workforce Training: Prioritize user education to defend against threats like phishing attacks and Multi-Factor Authentication (MFA) bypass.
- Adopt Security-First Culture: Instill a culture where every individual within the organization, not just security personnel, prioritizes security in decision-making and actions.
- Continuous Monitoring: Vigilantly monitor all assets, including physical devices, websites, and social media accounts, to detect and address potential risks.
- Threat Intelligence: Harness threat intelligence from the Dark Web to understand how threat actors operate and ascertain their goals.
- Third-Party Risk Management: Identify and mitigate risks within the organization’s software and systems, as well as those associated with third-party suppliers and partners.
In conclusion, the escalating APAC cybersecurity threats demand a multifaceted defense approach. Organizations must prioritize user education, continuous monitoring, and a security-first culture to effectively combat phishing, infostealers, MFA bypass, ransomware, software supply chain vulnerabilities, hacktivism, and risks associated with generative AI. A proactive strategy, informed by threat intelligence, is essential to navigate the complex and evolving cybersecurity landscape in the region.
Read next: SecurityHQ reveals the top 5 cybersecurity concerns from its latest threat advisories








